After reading this post, you’ll understand what torrenting is and how it works. With this knowledge, you’ll know how to torrent correctly (safe and fast). You’ll understand the BitTorrent protocol’s vulnerabilities and where you should protect yourself, whether you need a VPN, proxy, or seedbox. You’ll also learn how to download your torrents faster.
What is Torrenting?
Torrenting is the process of using the P2P file-sharing BitTorrent protocol to share or transfer files simultaneously with multiple peers and across the public Internet [Torrent Definition].
To understand how the torrenting process works, let us dig into some of its various components:
- The Torrent Metadata. Torrent files are the files you download before downloading content. They contain metadata, including data’s size, contents, structure, and a list of torrent tracker servers. Remember that torrent files do not include the data itself, just the instructions for getting the data. You can obtain torrent metadata via a torrent file (.torrent) or through a URL magnet. The file-less way to load torrents is via URL magnet links. A magnet link helps you load a torrent into a torrent client without a (.torrent) file. They identify files via cryptographic file hash values.
- The Torrent’s Content. As mentioned above, a torrent file does not contain the content; it just includes the metadata (instructions on downloading the content). The content itself is distributed across users’ machines and servers. You could have a portion of the content and still be able to upload it to other users (and vice versa).
- The Torrent Client: The torrent client is a vital element for P2P file-sharing. It reads the torrent, connects with the torrent server (the tracker) and with the peers, and puts together all the downloaded pieces of content. Examples of popular torrent clients are uTorrent, Deluge, and qBitorrent. Modern torrent clients come with features like DHT (tracker-less method), superseeding, PEX, URL magnet support, tracker creating, built-in player, built-in search engine, and more.
- Torrent Swarm. A torrent swarm is a vital component of the BitTorrent protocol. It is a group of peers (seeders or leechers) with a common interest in a particular piece of content. A torrent swarm builds up to share or download specific content. Torrent swarms can be large groups (when a torrent is healthy), small (when the torrent is unhealthy), and non-existent (when the torrent file is still around, but there is no one sharing the content and participating in the swarm).
- The Torrent Tracker. Torrent trackers are servers that establish and maintain communications for torrent swarms. When you load a torrent into a torrent client, the client reads the torrent file information and connects to the torrent tracker indicated in the file. Torrent trackers can be private or public. Private torrents from private trackers add a user’s passkey to protect their torrents from being used outside their private domain. Public trackers, on the other hand, do not add any passkey to the torrent file, so they are free and open to use by anyone.
- A Torrent Indexer. Although not a component of the BitTorrent protocol, torrent indexers are very important in torrenting because they help users search, browse, and find the content they are looking for. Torrent indexers are the popular torrent websites open to the public, such as Limetorrent, TPB, or RARBG. On the other hand, there are also closed private torrent indexers with rich and niche content libraries.
What is the Process of Torrenting?
Refer to the diagram below. The torrent swarm comprises uploaders (seeders) and downloaders (leechers). The uploader does not need to upload the content as it already has a full copy of the content. Downloaders, on the other hand, upload and download pieces of the file. When a downloader has a full copy of the file, it becomes a seeder, or full uploader.
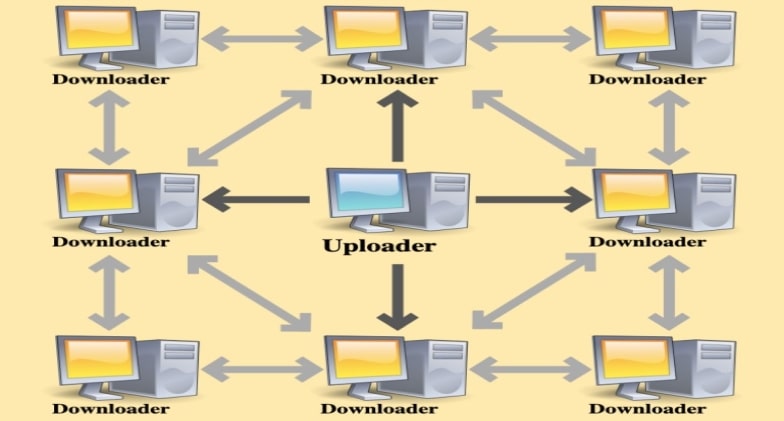
So now that you understand the critical concepts of torrenting, let’s see how it all binds together.
- The first step to torrenting would be to determine the content you want to download and find either a torrent file or magnet URL. You can find these on torrent indexers (either public or private).
- Once you get your file (or URL), you’ll need to load it into the BitTorrent client. Remember that although modern torrent clients support magnet URLs and DHT, not all do.
- When you load the torrent into your client, the client (with the help of the torrent tracker) will connect to the torrent swarm. In other words, your torrent will connect with other torrent peers with the content you are also looking for.
- If the torrent file you download is healthy (has a large torrent swarm), the content will likely download fast, but if the swarm is unhealthy (has a few seeders), you’ll probably have difficulty downloading the content.
Frequently Asked Questions (FAQ) about Torrenting and Torrents.
a. How to determine if the torrent is healthy?
A torrent is healthy if it has a large torrent swarm, which means there are many peers, seeders, and leechers. When you find a torrent on a website, ensure it has many peers (especially seeders). The more seeders a torrent has, the more chances you will download it and the faster it will be.
b. Is torrenting legal?
The problem with torrents is that the pirate community has adopted them to distribute copyright content. And so it has gained a bad reputation, but the truth is that torrenting (the activity) is not illegal, as long as you are not downloading copyrighted content. The technology itself is legal, but what you do with it can make all the difference. Big companies like Facebook or Twitter have used it internally to distribute updates to their global servers, and so does universities, governments, and other institutions like research and lab have used torrents to distribute large pieces of content.
c. Is torrenting safe?
Torrenting is safe if you are not downloading from untrusted tracker servers, know how to detect suspicious Malware or scam, and use private trackers whenever possible. Although you could torrent safely in public trackers, the truth is that hackers or attackers use these to spread their Malware by masking it under traditional media torrents.
d. How can someone track you while torrenting?
But for many good reasons, you always need protection while torrenting. The two most common BitTorrent vulnerabilities (where someone could track you) are within the unencrypted BitTorrent traffic and inside a torrent swarm. The BitTorrent traffic generated from your torrent client to the torrent swarm (if unencrypted) could easily be read by a middle-man (i.e., your ISP, government, local network admin, or even hackers) and mapped to you. The other place where someone could track you is in the torrent swarm. Since you are using your public IP to connect to the swarm, anyone within this swarm (including copyright trolls or hackers) could map (you) your IP, country, torrent client, OS, etc., with the content you are downloading.
e. How to protect yourself while torrenting?
So, if you read the above question, you’ll know that you need to protect your IP (mask it or hide it) and your BitTorrent traffic. There are three ways to do this, one with a proxy server, a VPN, or a seedbox. A seedbox is the best option to hide your IP and your traffic. Seedbox is a cloud-based server specially designed for torrenting; it provides high speeds and total privacy for torrenting.

